Ransomware attacks are the blackmailing of large and small enterprises around the world to pay many millions of dollars to recover their IT systems. In addition, there may be the cost of lawsuits caused by inadequate IT security, or even closure of the business. This can affect any organisation, as can be seen from the frequency of reports in the press.
What can you do to protect against and minimize the risk?
Organisations of all sizes must share and consume digital content from multiple sources and technologies. Unfortunately, this raises major cybersecurity risks as the content itself can be leveraged by cyber criminals and state actors to execute ransomware attacks.
Multiple security strategies, technologies and frameworks are used to minimise risk and damage caused by these unknown threats. However, seemingly daily there are reports of new successful ransomware attacks. These are often the result of unwitting staff targeted via email and web intrusions through social engineering, and compromised removable media being connected to corporate networks.
Traditional security methods that rely on signature-based vaccines, and “known” threat detection can be bypassed by complex scripting techniques which are recognised as legitimate processes. As ransomware and zero-day attacks constantly evolve to evade prevention technologies via malicious code within seemingly legitimate files, a comprehensive scanning, disarming and reconstruction (CDR) technology is required to ensure business continuity with minimal threat.
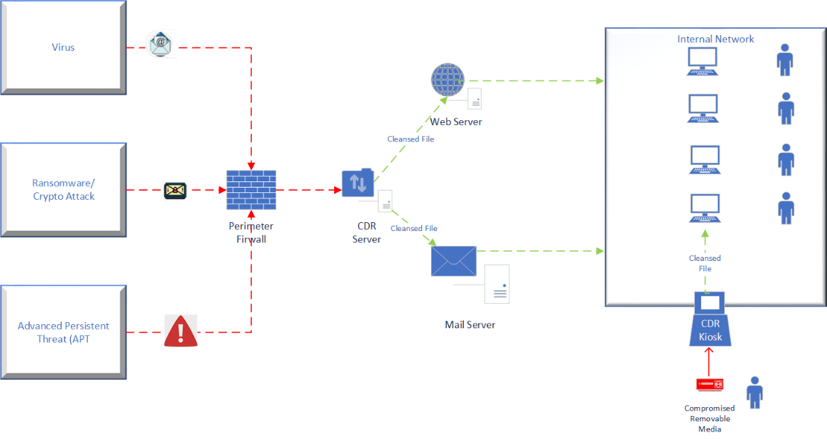
Content Disarm and Reconstruction (CDR) is a security technology which removes malicious and harmful code from otherwise valid files. As opposed to traditional anti-malware software, CDR does not determine or detect malware’s behaviour – rather it strips the file of all components which do not meet the organisations file format policies and definitions. The file is then reconstructed as a safe file which is forwarded to its intended recipients to enable business as usual processes without disruption.
This method provides a much more effective mechanism for preventing ransomware hidden within zero day and advanced persistent threat attacks.
Ransomware, destructive malware, insider threat actions and innocent user faults all present potential threats to organisations of all sizes. EB2BCOM can assist in creating an effective defence strategy utilizing industry best practice frameworks such as NIST and MITRE, tailored to the specific requirements of each individual organisations.
Our methodology:
Identify: Working with the organisation’s technology teams, EB2BCOM’s consultants will develop a map of all key assets within the organisation and produce a risk assessment pertaining to systems, staff, data and applications.
Protect: Using the unique patented Content Disarm and Recover technology from partner ODIX, EB2BCOM will develop, implement and configure safeguards and security controls against the critical data and application assets within the organisation’s technology environment.
Detect: Working with the organisation’s key technology staff, EB2BCOM will develop and implement effective security activities matched to the key assets to identify initiation and occurrence of cyber security threats.
Respond: EB2BCOM will produce specific use cases and security event patterns matched to the organisations business processes to take effective action on a detected cyber security incident.
Recover: EB2Bcom will work the key technology stakeholders and business owners to develop and maintain recovery strategies and plans to restore operations and maintain resilience on any infrastructure and services that were impacted by the security event.
EB2BCOM is an independent specialist in assessing and advising on cybersecurity risks, and in implementing solutions to address them. We have a particular capability and focus on prevention, and the core enabler of identity security.
We offer a flexible and tailored approach that offers an alternative to the “big ticket” offerings of large consultancies and integrators. Our clients include defence, security agencies, federal state, territories and local governments across Australia and Singapore.
We are an Australian-owned specialist with head offices in Australia and Singapore. We have been trading over 20 years, with an exemplary success record and a superb reputation for customer support.
EB2BCOM is Australian sales and implementation partner for odix. odix offer a range of products to protect your organisation from the proliferation of malware. Find out more at odi-x.com.